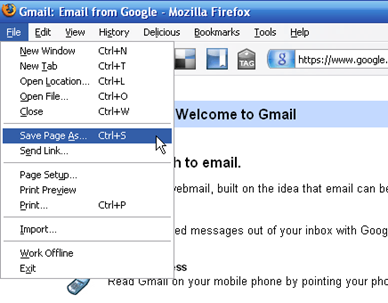
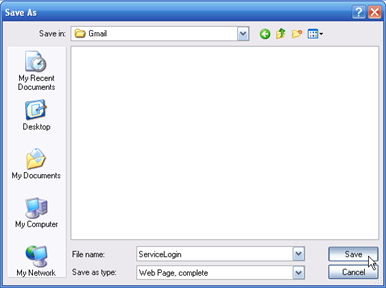
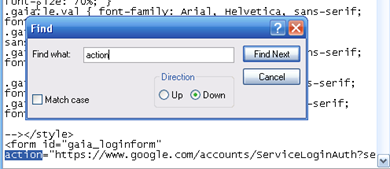
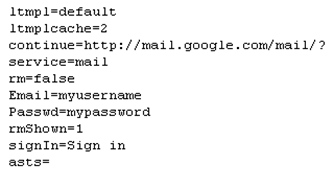
You can execute two types of commands from within the
command shell.The first type is an internal command—these commands are
built in the command shell itself and do not appear as executable files
anywhere in the system. Most of these commands are very similar to
MS-DOS commands. Examples of internal commands are Dir for generating a directory listing, Cls for clearing the screen, and Del for deleting a specific file.
The
second type of command you can execute from within the command shell is
an external command. External commands are separate executable files
located in the %SystemRoot\System32 folder. Although these are called external, they still run from within the command shell. Examples of external commands are XCOPY.exe for copying the entire directory tree, DISKPART.exe for managing disk partitions, and IPCONFIG.exe
for displaying the computer’s Transmission Control Protocol/Internet
Protocol (TCP/IP) configuration. External commands are more versatile
and offer more advanced capabilities than internal commands. Here are
list some of the more common internal commands:
■ Assoc Displays
or modifies the current filename extension associations. When ou use
this command without any parameters, it displays a list of all filename
xtension associations. For example, if you type assoc .doc at the
command rompt, the extension association will be displayed as
.doc=Word.Document.8.
■ Call
Used to call another batch program file or a procedure from within a
batch ile. Control of the currently running batch file is then
transferred to the called atch file.This command accepts labels as
arguments. It has no effect if you use it outside a batch file.
■ CD (ChDir)
Displays the name of the current working directory or changes the
current working directory. If you use it without any parameters, the
current working directory is displayed. For example, to change the
working directory to C:\Adminfiles\ Support, assuming your current working drive is C:, type cd \adminfiles\ support at the command prompt.
■ Color
Changes the foreground and background colors for the current session of
the command shell.This command has the same effect as using the cmd /t:FB
command discussed earlier.The parameters F and B are values of the
colors, For example, the command color 17 will change the foreground
color to blue and the background color to white.
■ Cls Clears the screen of the current command shell and erases the screen buffer, resulting in a blank command prompt window.
■ Copy
Copies the specified file from one location to another. If the source
and destination locations are the same, an error is returned that says “File cannot be copied on to itself.”
■ Date Displays or changes the current date on the computer.
■ Dir
Displays the contents of the current working directory, including names
of the subdirectories.You can specify a different directory and use
wildcards to limit the results.This command also displays the total
number of files and subdirectories, their size, total space used, and
space remaining on the drive.
■ Del (Erase) Deletes the specified file, multiple files, or all files within a given directory. For example, the command Del C:\Reports will delete all files in the C:\Reports folder.You can use wildcards to specify certain types of files to delete; for example, Del C:\Reports\*.doc will delete all files with a .doc extension in the C:\Reports folder.
■ Echo Displays text strings used with the command line and sets the echo on or off.This command is similar to using the command Cmd.exe /e:on | off. You can also use this command to display a message.
■ Endlocal Ends localization of the environment variables in a batch file and restores them to their values before the Setlocal command.This command works only in batch files and has no effect if you use it separately at the command prompt.
■ Exit Used to exit from the command shell window.
■ For
Used to run a specified command for each file in a set of files.You can
use it within a batch file or directly from the command prompt.
■ Ftype
Displays current file types or modifies the file types used in filename
extension associations. If you use it without any parameters, it
displays the file types that have open command strings defined.The open
command string specifies the open command used to open the file type.
■ Goto
Used to direct the command interpreter to jump to a command specified
with the label.You use it in batch files to direct the processing from
the command identified by the label.
■ If Used
in batch files to perform conditional processing of commands. If the
condition is satisfied, the command following the If command is
processed. Otherwise, the interpreter processes the command that follows
the Else command.
■Md (Mkdir) Creates a directory or a subdirectory. For example, Md C:\Reports\MyFiles or Mkdir C:\Reports\MyFiles will create a Myfiles subdirectory within the Reports directory on the C: drive.
■ Move
Moves one or more files from one directory to another.The source and
target locations of the files are specified in the command. If the
source is not specified, files are moved from the current working
directory.
■ Path
Displays or changes the command path for searching the executable
files. When you use this without any parameters, it displays the current
command path the operating system uses to search for executables.
■ Pause
Suspends the processing of a batch file and prompts the user to press
any key to continue processing. Using pause in a batch file is different
from using the Ctrl + C key combination.This key
combination stops the batch program from processing and asks the user
whether she wants to terminate the procedure.
■ PopD Changes the directory stored by the PushD command as the current working directory in a batch file.The PushD command creates a virtual directory, and repeated use of the PushD command creates a stack of multiple directories. The PopD command changes the current directory to the one most recently stored by PushD.
■ Prompt
Sets the display text for the command prompt.You use it to customize
the command prompt to display any text, such as the current date and
time.To reset the prompt to its default, use the Prompt command without
any parameters.
■PushD Stores the name of the current directory for use by PopD before changing to another specified directory.The directories are stored in a stack with the last directory on top.
■ Rd (Rmdir)
Removes or deletes the directory or directories and subdirectories
specified in the command.This command cannot delete a directory that has
hidden or system files.You must empty the directory before using this
command, and you cannot delete the current working directory.You must
first use the Cd command to change the current directory.
■ Rem Used to insert comments or remarks in a batch file.The text after the Rem command is not processed.
■Set
Displays, sets, or removes the environment variables. When you use this
command without any parameters, it displays the current environment
variables.The environment variables are used to control the behavior of
batch files.You would commonly use this command in the Autoexec.nt file.
■ Setlocal Starts localization of environment variables in a batch file.The localization ends when the command interpreter encounters the Endlocal command.This command is effective only in batch files.
■ Shift Changes the position of a replaceable parameter in a batch file.
■ Start
Opens a second command prompt window to run a specified program or an
executable. If no program or command is specified, the command just
opens another command prompt window.
■ Time Displays or changes the current time on the computer.
■ Title
Used to change the title of the command prompt window during the
processing of a batch file.You can reset the title to its default by
using the Title command again.
■ Type Displays the contents of a text file.This command does not modify the text file.
■ Vol Displays the volume number and serial number of a disk.